|

|
Quadrant 3: Complex Data without Queries (Cont.)
Open floor plan example (cont.)
- Using a file system, the compaction routine needs loading and converting the data, and then unloading and reconverting it.
- Using a persistent language, it becomes the language support system‘.s problem to load and unload as well as to convert it from disk format to main memory format and back.
|
|
|
J = J + 1
The above command is an update statement in a persistent language. To speed up, storage system and user program run in the same address space.
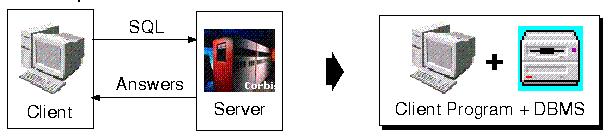
- Security problem
⇒A malicious program can use operating system calls to read and write any data that the storage system is capable of reading and writing. Because read and write calls for both the program and the storage system run in the same address space, the operating system can not distinguish them.