The following steps show how to perform public-key encryption (cont.):
- Generating the public key,
- Using the public key to generate the private key,
- Encrypting the text into ciphertext, and
- Decrypting the ciphertext into the original text.
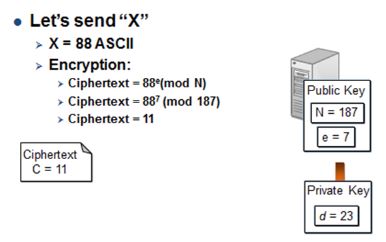
| Assume sending a single character; ‘X’. ASCII for X is 88. As we are the sender, we only know the public key’s 2 values: 187 and 7, or N and e. Running 88 through the simple algorithm gives us the value 11. We send the ciphertext value 11 to the ecommerce web server. |
|
Ciphertext = 88e ( mod N ), where public key = (N, e) Ciphertext = 887 ( mod 187 ) ∵ N=187 and e=7 Ciphertext = 11
|
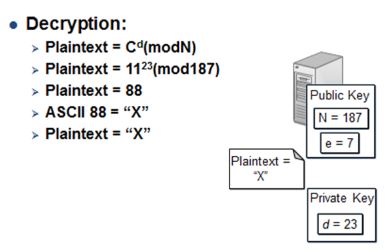
Decrypting the Ciphertext
The web server passes the plaintext through the algorithm shown above and gets us the original ‘X’ that was sent. |
|
Plaintext = Cd ( mod N ), where public key = N and private key = d Plaintext = 1123 ( mod 187 ) ∵ d=23 and N=187 Plaintext = 88 or ‘X’