Symmetric-key encryption only involves one key, and you just use that one key to both encrypt and decrypt a message. Whereas, public-key (asymmetric-key) cryptography is any cryptographic system that uses pairs of keys:
- Public key, which is a large numerical value that is used to encrypt data, and is made available to everyone through a publicly accessible repository or directory.
- Private key, which is another large numerical value that is mathematically linked to the public key. Whatever is encrypted with a public key may only be decrypted by its corresponding private key and vice versa.
- Authentication, where the public key verifies that a holder of the paired private key sent the message, and
- Encryption, where only the paired private key holder can decrypt the message encrypted with the public key.
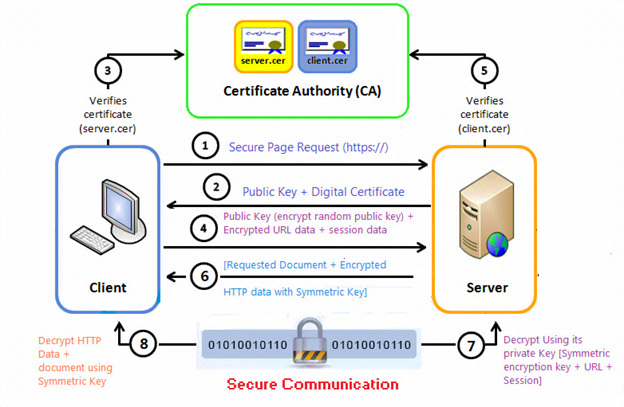
|



|
|
Hello everybody. What a great wedding that we’re at! Weddings, they have three rings. The first ring is the engagement ring. Then you have the wedding ring. Then, finally, you have the suffe-ring! — London Hughes |